Wednesday, November 28, 2007
How e-culture changes television model.

The faux-documentary style video is filmed daily on location and is also available via YouTube. The first episode was released on 15 June 2007.
The plot follows Dawn Jones who discovers in the opening episode that she is the child of a sperm donor and follows her travels around Europe to find her 26 siblings. It stars Emma Fryer in the lead role, with Neil Edmond as Ian, the first brother she locates and who travels with her.
Unusually, the production is released under a Creative Commons 'Attribution-Share alike' licence, allowing it to be freely re-edited, even commercially, and press coverage has considered it as 'Wikipedia-like' in allowing anyone to edit and contribute to the storyline.
The internet-only release on the back of the current mania for online social networking has also generated substantial independent blog review and analysis.
These young guys who have fortunes on the internet.
For some lucky and clever ones, what had begin as a little project had become a huge success story.
Two of the three co-founders of Paypal were 27 years old when they launched this system. Last semester, the buyings have increased of 34%, with 12,2 Md$.
Max Levchin
 was born in 1975. He is a Ukrainian-born American computer scientist and entrepreneur widely known as co-founder (with Peter Thiel) and former Chief technology officer of PayPal. Originally from Kyiv, Ukraine (then part of the Soviet Union), he moved to Chicago, Illinois in 1991. He received his bachelor's degree in computer science at the University of Illinois at Urbana-Champaign in 1997 and co-founded two companies that made Internet-tools, NetMeridian Software and SponsorNet New Media. In 1998, he founded Fieldlink with John Bernard Powers, which was later restructured to become Confinity and eventually PayPal. PayPal went public in February 2002, and was subsequently acquired by eBay. His 2.3% stake in PayPal was worth approximately $34 million at the time of the acquisition.He is primarily known for his contributions to PayPal's anti-fraud efforts and is also the co-creator of the Gausebeck-Levchin test, one of the first commercial implementations of a CAPTCHA. Meet him is this NerdTV interview.
was born in 1975. He is a Ukrainian-born American computer scientist and entrepreneur widely known as co-founder (with Peter Thiel) and former Chief technology officer of PayPal. Originally from Kyiv, Ukraine (then part of the Soviet Union), he moved to Chicago, Illinois in 1991. He received his bachelor's degree in computer science at the University of Illinois at Urbana-Champaign in 1997 and co-founded two companies that made Internet-tools, NetMeridian Software and SponsorNet New Media. In 1998, he founded Fieldlink with John Bernard Powers, which was later restructured to become Confinity and eventually PayPal. PayPal went public in February 2002, and was subsequently acquired by eBay. His 2.3% stake in PayPal was worth approximately $34 million at the time of the acquisition.He is primarily known for his contributions to PayPal's anti-fraud efforts and is also the co-creator of the Gausebeck-Levchin test, one of the first commercial implementations of a CAPTCHA. Meet him is this NerdTV interview. Like Levchin, Luke Nosek, born in 1975 too, is another co-founder of PayPal and serves now as The Funders Fund Vice President of Marketing and Strategy. While at PayPal, Luke oversaw the company's marketing efforts at launch, growing the user base to 1 million customers in the first six months. Luke also created "Instant Transfer," PayPal's most profitable product. Prior to PayPal, Luke was an evangelist at Netscape. Luke has also co-founded two other consumer Internet companies, including the web's first advertising network, and has made a number of venture investments since 2000. Luke received a B.S. in Computer Science from the University of Illinois, Urbana-Champaign.
Like Levchin, Luke Nosek, born in 1975 too, is another co-founder of PayPal and serves now as The Funders Fund Vice President of Marketing and Strategy. While at PayPal, Luke oversaw the company's marketing efforts at launch, growing the user base to 1 million customers in the first six months. Luke also created "Instant Transfer," PayPal's most profitable product. Prior to PayPal, Luke was an evangelist at Netscape. Luke has also co-founded two other consumer Internet companies, including the web's first advertising network, and has made a number of venture investments since 2000. Luke received a B.S. in Computer Science from the University of Illinois, Urbana-Champaign.Wednesday, November 14, 2007
Should the police be involved in online murders announcements?

Tuesday 8th November 2007, seven schoolchildren and their principal were killed when a student opened fire in a town near Helsinki, in the deadliest shooting in Finland's history. The gunman shot himself in the head and died later in hospital.
The 18-year-old student, identified by police as Pekka-Eric Auvinen, started shooting with a handgun during lessons yesterday at the Jokela secondary school in Tuusula, killing five boys and two girls as well as the principal, Helena Kalmi, police said at a news conference.
Two hours before police learned of the shootings, the gunman posted a warning with pictures of the campus and an armed man on YouTube, an online video service of Google Inc., officials said.
Ten children were treated for minor injuries at Hyvinkaeae hospital in a town near the school, Ulla Keraenen, a senior surgeon there, said in a telephone interview. None of the children had been shot, she added.
Tuusula is a town of about 35,000 people 30 kilometers (19 miles) north of the capital.
Rescue Crews
Police were called to the school at 11:43 a.m. local time yesterday. Officers were on the scene 11 minutes later and tried to talk to the gunman, who fired one shot at them without hitting anyone. Rescue crews had to evacuate pupils, teachers and other school workers through the windows.
Searchers found the attacker injured shortly after 3 p.m., according to the Tuusula municipality Web site. The gunman and most of his victims were found in the lower lobby of the building, police said. (bloomberg.com)
The question coming after this is : Should the police be involved ahead of the act in cases like this? We have to keep in mind that we are in a growing trend (recall the case in Virginia Tech)
It is sure, the police can't listen to all desperate teenagers of the word who post videos of them on Youtube. It would cost too much employees, time and money.
On the other hand, things have to change. Until this happens again. I don't have any ideas about what is technologically possible. But it seems to me that Youtube have a surveillance system. They may apply it to the videos containing dark messages and they may transfer it to the police. So maybe they could act on time.
Google : cannibal or super heroe ?
 Everyday, Google is becoming bigger, offering new services. Even if, they are not. For example, Google begins hosting content from 4 news services on its own site The Associated Press instead of only sending readers to other destinations.
Everyday, Google is becoming bigger, offering new services. Even if, they are not. For example, Google begins hosting content from 4 news services on its own site The Associated Press instead of only sending readers to other destinations.The change affects hundreds of stories and photographs distributed each day by the AP, Agence France-Presse, The Press Association in the United Kingdom and The Canadian Press. It could diminish Internet traffic to other media sites where those stories and photos are also found — a development that could reduce the online advertising revenue of newspapers and broadcasters.
Google negotiated licensing deals with the AP and French news agency during the past two years after the services raised concerns about whether the search engine had been infringing on their copyrights. The company also reached licensing agreements with The Press Association and The Canadian Press during the same period.
Financial terms of those deals have not been disclosed.
The new approach does not change the look of Google News or affect the way the section treats material produced by other media.
Although Google already had bought the right to display content produced by all four news services, the search engine's news section had continued to link to other Web sites to read the stories and look at the photographs.
That helped drive more online traffic to newspapers and broadcasters who pay annual fees to help finance the AP, a 161-year-old cooperative owned by news organizations.
Now, Google visitors interested in reading an AP story will remain on Google's Web site unless they click on a link that enables them to read the same story elsewhere. Google does not have any immediate plans to run ads alongside the news hosted on its site.
Although the change might not even be noticed by many Google users, the decision to corral the content from the AP and other news services may irritate U.S. publishers and broadcasters if the move results in less traffic for them and more for Internet's most powerful company.
A diminished audience would likely translate into less online revenue, compounding the financial headaches of long-established media already scrambling to make up for the money that has been lost as more advertisers shift their spending to the Internet.
Google has been the trend's biggest beneficiary because it runs the Internet's largest advertising network. In the first half of this year, the 9-year-old company earned $1.9 billion (€1.4 billion) on revenue of $7.5 billion (€5.5 billion).
Despite Google's dominance in search, its news section lags behind several other rivals. In July, Google News attracted 9.6 million visitors compared with Yahoo News' industry-leading audience of 33.8 million, according to comScore Media Metrix.
Yahoo Inc., along with other major Web sites such as Microsoft Corp.'s MSN and Time Warner Inc.'s AOL, have been featuring AP material for years.
Under its new approach, Google reasons readers would not have to pore through search results listing the same story posted on different sites. That should in turn make it easier to discover other news stories at other Web sites that might previously have been buried, said Josh Cohen, the business product manager for Google News.
"This may result in certain publishers losing traffic for their news wire stories, but it will allow more room for their original content," Cohen said.
Vlae Kershner, news director for the San Francisco Chronicle's Web site, backed up that theory, saying Google News mostly refers readers interested in the newspaper's staff-written stories. "This is going to have a very minimal impact on our traffic," he said.
Referrals from Google News accounted for 2.2 percent of the traffic at newspaper Web sites during the week ending Aug. 25, according to the research firm Hitwise.
Caroline Little, chief executive and publisher of Washingtonpost.Newsweek Interactive, said she worries about anything that might erode her site's advertising revenue. "That's how we make money," she said. "We will be watching this carefully."
For its part, the AP intends to work with Google to ensure readers find their way to breaking news stories on its members' Web sites, said Jane Seagrave, the AP's vice president of new media markets.
In recognition of the challenges facing the media, the AP froze its basic rates for member newspapers and broadcasters in the U.S. this year.
That concession has intensified the pressure on AP to plumb new revenue channels by selling its content to so-called "commercial" customers on the Web. Those efforts helped the not-for-profit AP boost its revenue by 4 percent last year to $680 million (€496 million).
"AP relies on its commercial agreements to help pay the enormous costs of covering breaking news around the world, ranging from deadly hurricanes and tsunamis to conflicts like the war in Iraq," Seagrave said.
This example shows us that the proliferation of Google services is the hardest thing that the competitors could have supported.
How creativity is being strangled by the law ( Larry Lessing Conference)
Wednesday, November 07, 2007
Let's talk about trust on the internet.
Prosper permits to people to lend for free, to borrow and to be in an online community. People who need money request it, and other people bid for the privilege of lending it to them. Prosper makes sure everything is safe, fair and easy. Prosper is the go-between who allows exchanges and who shakes that trust is not is not violated.
In all communities, above all when there are economical exchanges, everything is based on trust originaly. The garantee offered by Prosper permits not to detract the operations.
There are a lot of sites like that: Ebay, Etrade...
The expansion of the Web 2.0 solution where we find always more interactivity and direct exchanges, people-to-people, make me think that we will find more sites like Prosper in the future.
I am back
After a thesis on webcomics and few vacation, I am back with you for a year to dicuss about e-culture.
Thursday, January 18, 2007
Backup your records and save your life
So now I keep my external memory bar and my usb keys always with me....
“FaceBook stalking”

"Facebook stalking" is the term that has developed for this typically harmless practice of finding people (or finding their profiles, at least) on Facebook and learning about them without their knowledge or consent. "It's a lot easier than the real thing," said freshman Abe Del Rio. Facebook stalking is mostly harmless and used to find out someone's e-mail to coordinate a class project or to discover other people on campus with common interests and tastes.
But it isn't just students that are Facebook stalking anymore. Campus security and residence life staffs have begun using pictures posted on the social networking site to find and prosecute students for alcohol violations. At Western Washington University, four students were placed on probation and one was asked to leave the housing system based on alcohol violations that were documented and discovered through Facebook.Privacy pollution, the modern freedom robbery

The expression “privacy pollution” refers to a diary problem we all know: the "junk" mails and the spams. We all receive every day newletters about the new technologies to enlarge our penis...
You see? That's it.
What are some of the concerns?
E-mail spam is the most common form of internet spamming. It involves sending unsolicited commercial messages to many recipients. Unlike legitimate commercial e-mail, spam is generally sent without the explicit permission of the recipients, and frequently contains various tricks to bypass e-mail filtering.
Spammers obtain e-mail addresses by a number of means: harvesting addresses from Usenet postings, DNS listings, or Web pages; guessing common names at known domains (known as a dictionary attack); and "e-pending" or searching for e-mail addresses corresponding to specific persons, such as residents in an area. Many spammers utilize programs called web spiders to find e-mail addresses on web pages (see also address munging). Many e-mail spammers go to great lengths to conceal the origin of their messages. They might do this by spoofing e-mail addresses (similar to Internet protocol spoofing). The spammer will modify the e-mail message so it looks like it is coming from another e-mail address. However, many spammers make it easy for recipients to identify their messages as spam by placing an ad phrase in the From field. Spammers try to circumvent the email filters by intentionally misspelling common spam filter trigger words.
For example, "viagra" might become "vaigra", or other symbols may be inserted into the word as in "v/i/a/g./r/a". E-mail service providers have begun to use the misspellings themselves as a filtering test. The most dedicated spammers—often those making a great deal of money or engaged in illegal activities, such as the pornography, casinos and Nigerian scam businesses—are often one step ahead of the providers. Retail e-mail services are updated constantly with improved spam filters, keeping track of spammers' technological progress by examining e-mails their users report as spam (many providers today have a prominent button to report spam). So-called "spambots" are a major producer of e-mail spam. The worst spammers create e-mail viruses that render an unprotected PC a "zombie computer"; the zombie will inform a central unit of its existence, and the central unit will command the "zombie" to send a low volume of spam. This allows spammers to send high volumes of e-mail without being caught by their ISPs or being tracked down by antispammers; a low volume of spam is instead sent from many locations simultaneously.
Bill Gates, speaking at the World Economic Forum in Davos in January 2004, predicted that spam would soon be "a thing of the past", and that Microsoft was working on several temporary solutions, as well as on a permanent "magic solution", to spam.
The California legislature found that spam cost United States organizations alone more than $10 billion in 2004, including lost productivity and the additional equipment, software, and manpower needed to combat the problem.
Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the kinds of spam messages sent, from the ways spammers send them, and from the arms race between spammers and those who try to stop or control spam. In addition, there are the opportunity cost of those who forgo the use of spam-afflicted systems. There are the direct costs, as well as the indirect costs borne by the victims - both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, identity theft, data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing.
It is complicated to fight it because spamming itself abridges the historical freedom of the Internet, by attempting to force users to carry the costs of material which they would not choose.But there are actions, as I will explain it here.
An ongoing concern expressed by parties such as the Electronic Frontier Foundation and the ACLU has to do with so-called "stealth blocking", a term for ISPs employing aggressive spam blocking without their users' knowledge.
These groups' concern is that ISPs or technicians seeking to reduce spam-related costs may select tools which (either through error or design) also block non-spam e-mail from sites seen as "spam-friendly". SPEWS is a common target of these criticisms. Few object to the existence of these tools; it is their use in filtering the mail of users who are not informed of their use which draws fire. Some see spam-blocking tools as a threat to free expression—and laws against spamming as an untoward precedent for regulation or taxation of e-mail and the Internet at large. Even though it is possible in some jurisdictions to treat some spam as unlawful merely by applying existing laws against trespass and conversion, some laws specifically targeting spam have been proposed.
In 2004, United States passed the Can Spam Act of 2003 which provided ISPs with tools to combat spam. This act allowed Yahoo! to successfully sue Eric Head, reportedly one of the biggest spammers in the world, who settled the lawsuit for several thousand U.S. dollars in June 2004.
Examples of effective anti-abuse laws that respect free speech rights include those in the U.S. against unsolicited faxes and phone calls, and those in Australia and a few U.S. states against spam. In November 2004, Lycos Europe released a screensaver called make LOVE not SPAM which made Distributed Denial of Service attacks on the spammers themselves. It met with a large amount of controversy and the initiative ended in December 2004.Court cases Attorney Laurence Canter was disbarred by the Supreme Court of Tennessee in 1997 for sending prodigious amounts of spam advertising his immigration law practice. Robert Soloway lost a case in a federal court against the operator of a small Oklahoma-based Internet service provider who accused him of spamming. U.S. Judge Ralph G. Thompson granted a motion by plaintiff Robert Braver for a default judgment and permanent injunction against him. The judgment includes a statutory damages award of $10,075,000 under Oklahoma law. In the first successful case of its kind, Mr. Nigel Roberts from the Channel Islands won £270 against Media Logistics UK who sent junk e-mails to his personal account.
Thursday, January 11, 2007
Youtube personal pages implication
When you create a personal page on you tube, it can have a lot of implications. Why?
First of all, because you enter in a community which is uge because Youtube is incredibly popular. This makes you involved in the web life and in the activity you chose. For example, if you upload videos you will have a lot of contact in this sector and you will be free to creates new pages with others youtube guys.
You can also be implicated in the web economic life if someone have noticed you for your talents or originality. It involves too the question of artistic property. If your production is at a buzz start, you artistic or entertainment life will change.
For me, the best use of Youtube profile is the professional one.
I think it is really helpful when for example you have an association without financial suppport. It is the best advertisement in terms of rentability and exposition. You are sure to find a public. It is the same thing for young artists who can express themselves in this site without technical matters. I show you here what I mean by the way of an animation picture.
Even in the big companies, the e-cv is a good thing to see how the employees behave themselves behind new technologies. It is a new way to evaluate the candidate, who is more free to present himself with his own words. i think this is a good invention but not for everybody. There are people who are no used to be filmed. They could fill really ill at ease to present themselves in a professional way in front of a camera. For me it is important to respect this. We have to let people chose how he wants to present himself.
The results are amazing. There is an example of e-cv I found of You Tube.
Enjoy.
A definition of the web content management system

A content management system (CMS) is a computer software system used to assist its users in the process of content management. A CMS facilitates the organization, control, and publication of a large body of documents and other content, such as images and multimedia resources. A CMS often facilitates the collaborative creation of documents. A web content management system is a content management system with additional features to ease the tasks required to publish web content to Web sites.
We generally use it for storing, controlling, versioning, and publishing industry-specific documentation such as news articles, operators' manuals, technical manuals, sales guides, and marketing brochures. It may support the following features:
- Import and creation of documents and multimedia material
-Identification of all key users and their content management roles
- The ability to assign roles and responsibilities to different content categories or types.
- The definition of the content workflow tasks, often coupled with event messaging so that content managers are alerted to changes in content.
- The ability to track and manage multiple versions of a single instance of content.
- The ability to publish the content to a repository to support access to the content. Increasingly, the repository is an inherent part of the system, and incorporates enterprise search and retrieval.
For example, we use it right now on this blog. We made a wiki in my class where we also use CMS.
Thursday, November 09, 2006
What SHTTP means.
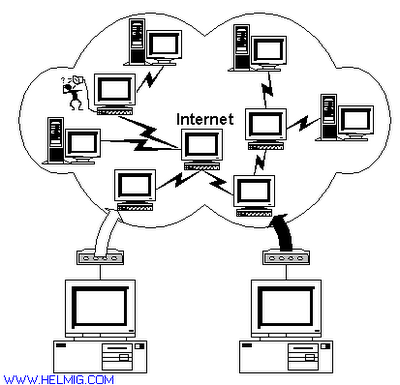
SHTTP means Secure Hypertext Transfer Protocol which is developed by Enterprise Integration Technologies in 1995 to ensure security with commercial transactions on the Internet. A protocol that provides secure transactions over the Web. It is endorsed by a variety of organizations. An extension to the HTTP protocol to support sending data securely over the World Wide Web. Not all Web browsers and servers support S-HTTP. Another technology for transmitting secure communications over the World Wide Web -- Secure Sockets Layer (SSL) -- is more prevalent. However, SSL and S-HTTP have very different designs and goals so it is possible to use the two protocols together. Whereas SSL is designed to establish a secure connection between two computers, S-HTTP is designed to send individual messages securely. Both protocols have been submitted to the Internet Engineering Task Force (IETF) for approval as a standard.
RSS
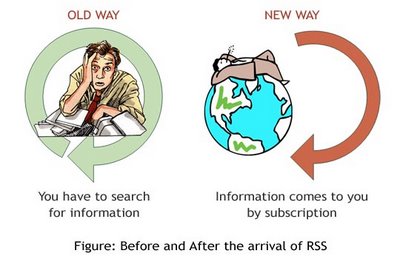
| What is RSS? | ||
| The Internet today contains a wealth of information. Avid Internet users visit many interesting websites and read many articles. Information and web pages make their way in to the favorite folder for later viewing. Over the course of time, re-visiting these bookmarks becomes a major task for users especially as the number of bookmarks grows. A better technique for users is to automatically receive information about updates to their favorite websites. Internet users can employ special software, like newsreaders and RSS-aggregators, to organize RSS feeds and get automatic updates. Products like Active Web Reader allow you to read RSS files. Such types of programs go beyond simply reading. They also organize RSS feeds, manage updates, monitor website changes and search for information online. They can keep you automatically updated on the latest changes by checking RSS feeds and displaying items from them. | ||
Let's talk about cybercrime.

According to Wikipedia, cybercrime is a term used broadly to describe criminal activity in which computers or networks are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime. This term is also used to include traditional crimes in which computers or networks are used to enalbe the illicit activity. Examples of cybercrime in which the computer or network is a tool of the criminal activity include spamming and certain intellectual property and criminal copyright crimes, particularly those facilitated through peer-to-peer networks.
Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating access controls), malicious code, and denial-of-service attacks.
Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, telecom fraud) and certain financial frauds. Finally, examples of traditional crimes facilitated through the use of computers or networks include Nigerian 419 or other gullibility or social engineering frauds (e.g., "phishing"), identity theft, child pornography, online gambling, securities fraud, etc.
Cyberstalking is an example of a traditionl crime -- harrassment -- that has taken a new form when facilitated through computer networks. Additionally, certain other information crimes, including trade secret theft and economic espionage, are sometimes considered cybercrimes when computers or networks are involved.
Cybercrime in the context of national security may involve hacktivism (online activity intended to influence policy), traditional espionage, or information warfare and related activities. Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud.
Here a the principal hackers of the time.
Apart from Tsutomu Shimomura, the other three hackers mentioned here were criminals at some point of time and for various reasons. They have all repented for their actions and are currently contributing in positive ways to the burgeoning cyber realm. It is interesting in retrospect to take note of when, why and how they turned to crime. Tsutomu, however, is recognized for bringing down Kevin Mitnick, arguably the most notorious hacker ever. The I-Love-You virus and the Sasser worm had caused so much damage without apparent human intervention that they too deserve due recognition.
Kevin Poulsen
Probably one of the most talented hackers of all time, Kevin Poulsen wanted more than what his high paid job could offer him. His crimes ranged from stealing classified military data to hacking into a radio station’s telephone lines in order to “win” a Porsche. He did not call himself the “Dark Dante” for nothing.
Kevin Mitnick
Well-known in the annals of the FBI, he was one of the most slippery crooks the bureau ever tried to apprehend. As proficient at actually committing the crime as he was at deceiving the authorities, he left a remarkable trail of crime as long as he was on the run. He had delved so deep into cybercrime that he was barred from using a computer for a long time after he was caught.
Adrian Lamo
This is the classic case of a white hacker who went too far.
Tsutomu Shimomura
A high profile researcher at
I love you Virus
This virus is notorious throughout the world. A highly effective self-replicating algorithm coupled with an instantly provocative message like “ Kindly check the attached LOVELETTER from
Sasser Worm
This malware does not even need a provocative message to have people loading it onto their computers – it comes and goes as it pleases. Being connected to the Internet is enough to get it loaded onto one’s computer and though it did not directly cause damage, it caused severe network disruptions worldwide leading to millions lost due to loss of productivity. Imagine the impact this had on hospitals and banks.
I would like to finish this presentation by one of the most important cybercrime story of the 20th. The american government called it "electronic Pearl Harbor".
For two days in January 1999, hackers repeatedly tapped into military computers at Kelly Air Force Base in
NBC News has learned the attack was a sophisticated, coordinated assault through computer networks in
The hackers didn't receive top secrets but the Pentagon's No. 2 man, Deputy Secretary of Defense John Hamre, says the
For the past several months, so-called cyberterrorists, operating from as many as 15 locations worldwide, have launched a series of coordinated attacks on Pentagon computers -- as many as 100 per day.
The attackers remain unidentified and since anyone with a computer is a potential enemy, experts warn the
Among the computers targeted were those of the Air Intelligence Agency, the Air Force Information Warfare Center and a Joint Chiefs of Staff command-and-control operation. Officials said it was the most sophisticated attack yet on Pentagon computers.
The attack so worried the Pentagon that it called in the FBI, which has launched a criminal investigation. 
Several experts said such an attack wouldn't have even been detected at all a few months ago but the government has been quietly setting up cyberwar early-warning operations at the Pentagon, CIA and the National Security Agency over the past year.
Without falling down the paranoïa, we all have to be careful. I have never been a victim of cybercrime but I am a possible target as all Internet users. In fact, as soon as we pay something on internet ,our bank code can be stolen.
However, the protection is making progress. Some sure systems are applied as Paypal for example, and work well.
Tuesday, November 07, 2006
Why Youtube is so great.
Today, nearly all Internet users know or have heard about Youtube. It is the symbol of the last innovation of the NTIC, the Web 2.0.
What is you Tube?
YouTube is a popular free video sharing web site which lets users upload, view, and sharevideo clips. Founded in February 2005 by three employees of PayPal, the San Bruno-based service utilizes Adobe Flash technology to display video. The wide variety of site content includes movie and TV clips and music videos, as well as amateur content such as videoblogging. It is staffed by 67 employees. In October 2006, Google, Inc., announced that it had reached a deal to acquire the company for $1.65 billion USD in Google's stock. The acquisition is expected to close in the fourth quarter of 2006.
The company's humble beginnings in a garage and commitment to offering free services necessitated outside financial backing. In November of 2005, venture capital firm Sequoia Capital invested an initial $3.5 million; additionally, Roelof Botha, partner of the firm and former CFO of PayPal, joined the YouTube board of directors. In April 2006, Sequoia put an additional $8 million into the company, which had experienced a boom of popularity and growth in just its first few months.
At present, YouTube is one of the fastest-growing websites on the World Wide Web, and is ranked as the 10th most popular website on Alexa, far outpacing even MySpace's growth. According to a July 16, 2006 survey, 100 million clips are viewed daily on YouTube, with an additional 65,000 new videos uploaded per 24 hours. The site has almost 20 million visitors each month, according to Nielsen/NetRatings, where around 44% are female, 56% male, and the 12- to 17-year-old age group is dominant. Youtube's pre-eminence in the online video market is staggering. According to the website Hitswise.com, Youtube commands up to 64% of the
The key of this success is, in my opinion, the speed of download and the fact it is free. Everyone can use it, even if he or she's not a king of the internet. We can explain this success by the buzz it had created when it started. Youtube has revealed people, who are famous in the website
community. As an example, I will present the lonelygirl15 phenomenon.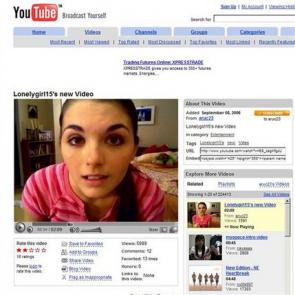
Lonelygirl15 is a fictional video blog that came to international attention via YouTube, a popular video sharing website. The central character is a YouTube user of the same name, although she is commonly known as Bree. The character achieved massive popularity with her series of videos, which acquired over 15 million cumulative views. But after viewers grew suspicious, lonelygirl15 was exposed as a fictitious character played by
The series, which began June 16, 2006 is still running, with new videos appearing regularly.The series, which began June 16, 2006 is still running, with new videos appearing regularly.
As far as I am concerned, I use Youtube everyday. I only watch videos, like musical clips and series. I don't donwload movies, that it why I don't share what I watch. I don't like to download because when I do it I feel like robbing something. I don't feel at ease. One of the reason why I like Youtube is that it is now allowed. Must of all, it is not necessary to download because we can see what we want, when we want and wherever there is an internet access. It is so much faster and safer that download sites like Emule or Napster, that it would be silly to not use it.
Thinking about the possible uses of Youtube in the future, we can all imagine. The best like the worst.
We can plan that people suffering of censorship will find here a way to get out of their silence. They have the public to read their message. We can also dream that some friendships and love stories will born. I think that it is already the case but I am sure that this movement will grow.
But stop dreaming, and let think about professional uses. Managers now have the possibility to edit methodology, secret of success or informations they want to transmit to their employees. When we see that the White House uses Youtube in her campaign against drugs, we can easily apply this to the company system. Youtube is as all the medias a way of pressure. Here comes the bad aspect. We know that all the files coming to Youtube are checked. But if the company, now forming part Google, is on lobbying, the game will be ended.