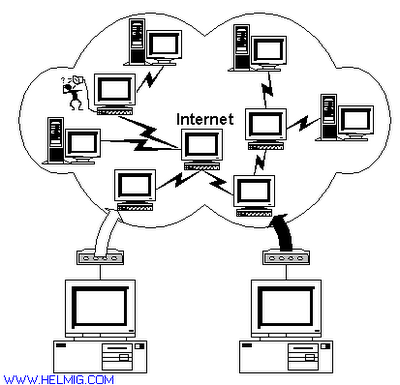
According to Wikipedia,
cybercrime is a term used broadly to describe criminal activity in which computers or networks are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime. This term is also used to include traditional crimes in which computers or networks are used to enalbe the illicit activity. Examples of cybercrime in which the computer or network is a tool of the criminal activity include spamming and certain intellectual property and criminal copyright crimes, particularly those facilitated through peer-to-peer networks.
Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating access controls), malicious code, and denial-of-service attacks.
Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, telecom fraud) and certain financial frauds. Finally, examples of traditional crimes facilitated through the use of computers or networks include Nigerian 419 or other gullibility or social engineering frauds (e.g., "phishing"), identity theft, child pornography, online gambling, securities fraud, etc.
Cyberstalking is an example of a traditionl crime -- harrassment -- that has taken a new form when facilitated through computer networks. Additionally, certain other information crimes, including trade secret theft and economic espionage, are sometimes considered cybercrimes when computers or networks are involved.
Cybercrime in the context of national security may involve hacktivism (online activity intended to influence policy), traditional espionage, or information warfare and related activities. Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud.
Here a the principal hackers of the time.
Apart from Tsutomu Shimomura, the other three hackers mentioned here were criminals at some point of time and for various reasons. They have all repented for their actions and are currently contributing in positive ways to the burgeoning cyber realm. It is interesting in retrospect to take note of when, why and how they turned to crime. Tsutomu, however, is recognized for bringing down Kevin Mitnick, arguably the most notorious hacker ever. The I-Love-You virus and the Sasser worm had caused so much damage without apparent human intervention that they too deserve due recognition.
Kevin Poulsen
Probably one of the most talented hackers of all time, Kevin Poulsen wanted more than what his high paid job could offer him. His crimes ranged from stealing classified military data to hacking into a radio station’s telephone lines in order to “win” a Porsche. He did not call himself the “Dark Dante” for nothing.
Kevin Mitnick
Well-known in the annals of the FBI, he was one of the most slippery crooks the bureau ever tried to apprehend. As proficient at actually committing the crime as he was at deceiving the authorities, he left a remarkable trail of crime as long as he was on the run. He had delved so deep into cybercrime that he was barred from using a computer for a long time after he was caught.
Adrian Lamo
This is the classic case of a white hacker who went too far. Adrian was a good friend of both Kevin Mitnick and Poulsen but he did not go to the extent that they went in the realm of cybercrime. His life, however, serves to remind all of us how easy it is to be seduced by the dark side even when one is actually working for the “good” side.
Tsutomu Shimomura
A high profile researcher at San Diego Supercomputer Center, Tsutomu has also worked with the likes of Richard Feynman. His other talent, hacking, was brought forth, however, when he had a run-in with Kevin Mitnick. Kevin had deliberately hacked into Tsutomu’s computer to steal some files and Tsutomu took it as a personal challenge to stop him as well as bring him to justice.
I love you Virus
This virus is notorious throughout the world. A highly effective self-replicating algorithm coupled with an instantly provocative message like “ Kindly check the attached LOVELETTER from me. ” has made this one of the most widely spread virus in history. It is believed that this virus alone caused over $10 billion in damages all over the world.
Sasser Worm
This malware does not even need a provocative message to have people loading it onto their computers – it comes and goes as it pleases. Being connected to the Internet is enough to get it loaded onto one’s computer and though it did not directly cause damage, it caused severe network disruptions worldwide leading to millions lost due to loss of productivity. Imagine the impact this had on hospitals and banks.
I would like to finish this presentation by one of the most important cybercrime story of the 20th. The american government called it "electronic Pearl Harbor".
For two days in January 1999, hackers repeatedly tapped into military computers at Kelly Air Force Base in San Antonio -- the center for the most sensitive Air Force intelligence, the kind of information critical to American troops now on patrol over Iraq and in Bosnia.
NBC News has learned the attack was a sophisticated, coordinated assault through computer networks in Canada, Norway and Thailand.
The hackers didn't receive top secrets but the Pentagon's No. 2 man, Deputy Secretary of Defense John Hamre, says the United States is essentially engaged in an all-out cyberwar.
For the past several months, so-called cyberterrorists, operating from as many as 15 locations worldwide, have launched a series of coordinated attacks on Pentagon computers -- as many as 100 per day.
The attackers remain unidentified and since anyone with a computer is a potential enemy, experts warn the United States military is vulnerable to a sneak attack.
At Kelly, the hackers were trying to enter a server that controls a number of sensitive computers at the base and other bases in the San Antonio area.
Among the computers targeted were those of the Air Intelligence Agency, the Air Force Information Warfare Center and a Joint Chiefs of Staff command-and-control operation. Officials said it was the most sophisticated attack yet on Pentagon computers.
The attack so worried the Pentagon that it called in the FBI, which has launched a criminal investigation. But the military is making some progress. New technology developed by the Navy did detect the attacks on Kelly Air Force Base, but failed to find the hackers themselves. 
Several experts said such an attack wouldn't have even been detected at all a few months ago but the government has been quietly setting up cyberwar early-warning operations at the Pentagon, CIA and the National Security Agency over the past year.
Without falling down the paranoïa, we all have to be careful. I have never been a victim of cybercrime but I am a possible target as all Internet users. In fact, as soon as we pay something on internet ,our bank code can be stolen.
However, the protection is making progress. Some sure systems are applied as Paypal for example, and work well.